
Headlines
March 9, 2026

Al Jazeera
Iran’s clerical body, the Assembly of Experts, has appointed Mojtaba Khamenei as Iran’s new supreme leader following the assassination of his father, Ali Khamenei, elevating the influential hardliner to lead the country through an escalating regional war while securing backing from the powerful Islamic Revolutionary Guard Corps.

Michael A. Smerconish
Daily Thoughts: Monday Musings
President Trump was hoping for an easy, Delcy Rodríguez (Venezuela) – like, outcome in Iran. A pliant leader even if it’s the same regime. He’s not getting it, at least not yet. Instead, the Iranians are trading one Khamenei for another. Meet the new boss, same as the old boss. That will forestall a coming disagreement between…

Axios
U.S. Dismayed by Israel Fuel Strikes
U.S. officials are privately alarmed after Israel carried out sweeping airstrikes on dozens of Iranian fuel depots, a scale of attacks that exceeded what United States officials expected and raised concerns the strikes could rally support for Iran’s regime and further drive up global oil prices.

NBC News
Oil Prices Surge to $100
Oil surged past $100 per barrel for the first time since July 2022 as the United States-Israel war with Iran disrupted global energy supplies and shipping through the Strait of Hormuz, rattling financial markets and raising fears that U.S. gasoline prices could soon approach $4 a gallon.

Times of Israel
Trump, Netanyahu on Iran Decision
In an interview with The Times of Israel, President Donald Trump said the decision on when to end the war with Iran will be made “mutually” with Israel PM Benjamin Netanyahu, emphasizing that while the Israeli prime minister will have input, he ultimately plans to make the final call on ending the conflict at the “right time.”

The Wall Street Journal
Netanyahu Got What He Wanted
Prime Minister Benjamin Netanyahu, once politically wounded by the Oct. 7, 2023 attack, is now pursuing what could become his defining strategic victory—toppling Iran’s Islamic Republic—after persuading President Donald Trump to join Israel in a joint campaign that could reshape the Middle East’s balance of power.
The Atlantic
Insider Trading Will Get People Killed
The rise of anonymous prediction markets like Polymarket is creating a dangerous national-security risk, as insiders with privileged knowledge of military operations could secretly profit from war-related bets—potentially tipping off adversaries and turning sensitive intelligence into a deadly market signal.

Axios
Special Forces Might Move on Nukes
The U.S. and Israel are weighing a potential special forces operation inside Iran to secure or neutralize its roughly 450 kilograms of highly enriched uranium—material that could be converted to weapons-grade within weeks—as part of broader efforts to prevent Tehran from obtaining a nuclear weapon.

The New York Times
Iran Could Still Retrieve Uranium
U.S. intelligence officials say Iran could potentially retrieve nearly 970 pounds of highly enriched uranium buried beneath the Isfahan nuclear site, raising new concerns for the Trump administration as it weighs risky options — including a possible commando raid — to prevent the material from being used to build a nuclear weapon.
USA Today
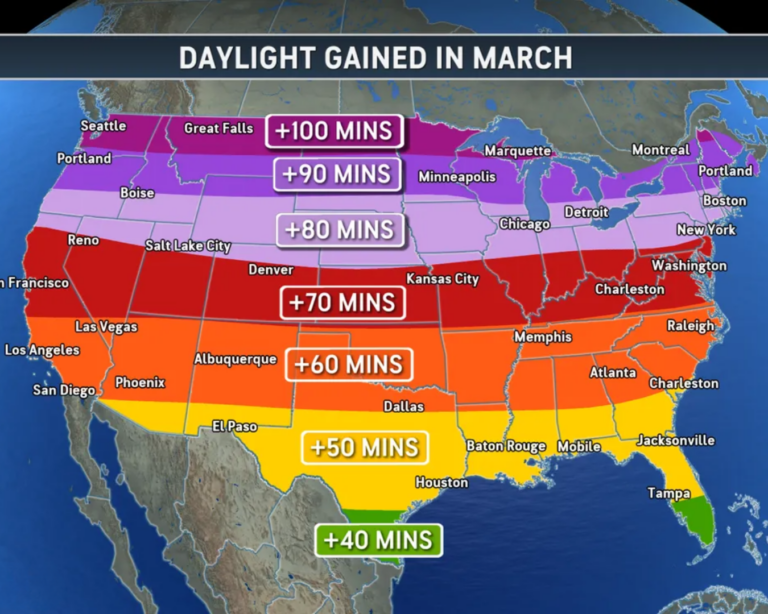
Sunlight Increasing, Not Due to DST
As AccuWeather meteorologists explain, the rapid jump in daylight during March isn’t caused by daylight saving time but by the Earth’s axial tilt, which turns the Northern Hemisphere more directly toward the sun and can add up to 90 minutes of extra daylight across parts of the United States by the end of the month.

The Hill
States Debate Time Change Laws
As most Americans move their clocks forward for daylight saving time, two states — Hawaii and much of Arizona — remain on permanent standard time while more than a dozen others push legislation to end the biannual clock change and adopt standard time year-round.

CNBC
TSA Straining in Shutdown Crisis
A TSA staffing shortage during the ongoing partial government shutdown is causing hours-long security lines at major U.S. airports—including Houston, Atlanta, and New Orleans—forcing travelers to arrive up to five hours early just as the busy spring-break travel season begins.

CBC
Americans Claim Canadian Citizenship
A new Canadian law, Bill C-3, removes the first-generation limit on citizenship by descent, potentially allowing millions of Americans with Canadian ancestry to claim citizenship — though applicants must first prove their lineage through official records and historical documents.

CBS News
Havana Syndrome Cover-Up?
Former CIA officer Marc Polymeropoulos is accusing the CIA of burying evidence related to Havana Syndrome after a classified mission reportedly obtained a portable microwave-based weapon that could explain the mysterious neurological injuries suffered by U.S. officials overseas.

New York Post
Bombs Thrown at Gracie Mansion
Two self-radicalized ISIS sympathizers allegedly threw a homemade IED packed with TATP explosive during a violent protest outside NYC Mayor Mamdani’s residence, prompting an investigation by the NYPD and the FBI after the device fortunately failed to detonate.

The Wall Street Journal
40 Famous Names in Epstein Files
The release of newly unsealed Jeffrey Epstein files has exposed connections between the disgraced financier and dozens of prominent figures across politics, business, academia, and royalty, prompting public apologies, resignations, and in some cases arrests.

Mediaite
Imminent Threat or Opportunity?
Defense Secretary Pete Hegseth dismissed a question from CBS’s Major Garrett about whether Iran posed an imminent threat before U.S. strikes, calling the debate “silly and academic” while defending the intelligence and timing behind the operation.

The New York Times
It's Not Just the Jeep Wave
Car enthusiasts across brands like Jeep, Porsche, Mazda, Subaru, and Land Rover follow quirky, unwritten rituals—from waves and headlight flashes to rubber-duck “gifts”—that signal belonging within their vehicle’s unique driver community.

Fox News
The Need for Noble Masculinity
Eric Hogue argues that declining college enrollment, workforce participation, and rising loneliness among young men reflect a deeper cultural problem, urging families, schools, and communities to restore higher expectations, mentorship, and “noble masculinity” to help boys develop discipline, purpose, and responsibility.

Variety
Country Joe McDonald Dies
Country Joe McDonald, the frontman of Country Joe and the Fish and a defining voice of the 1960s antiwar counterculture, has died at 84 after battling Parkinson’s disease, remembered for his provocative performance of “I-Feel-Like-I’m-Fixin’-to-Die Rag” at Woodstock that became an enduring symbol of Vietnam War protest.
For the Left
For the Right
Independent doesn’t mean indecisive.








